- ESTABLISH TEAM MEMBERS AND PROJECT GOALS
- ESTABLISH DEVELOPMENT GOALS WITH ULTRALIFT
- RECEIVED PATENT FOR DERIVING/TRANSFER OF DATA FROM TRAILER LANDING GEAR
- FINALIZE TEAM AGREEMENTS AND PARTNERSHIP WITH ULTRALIFT
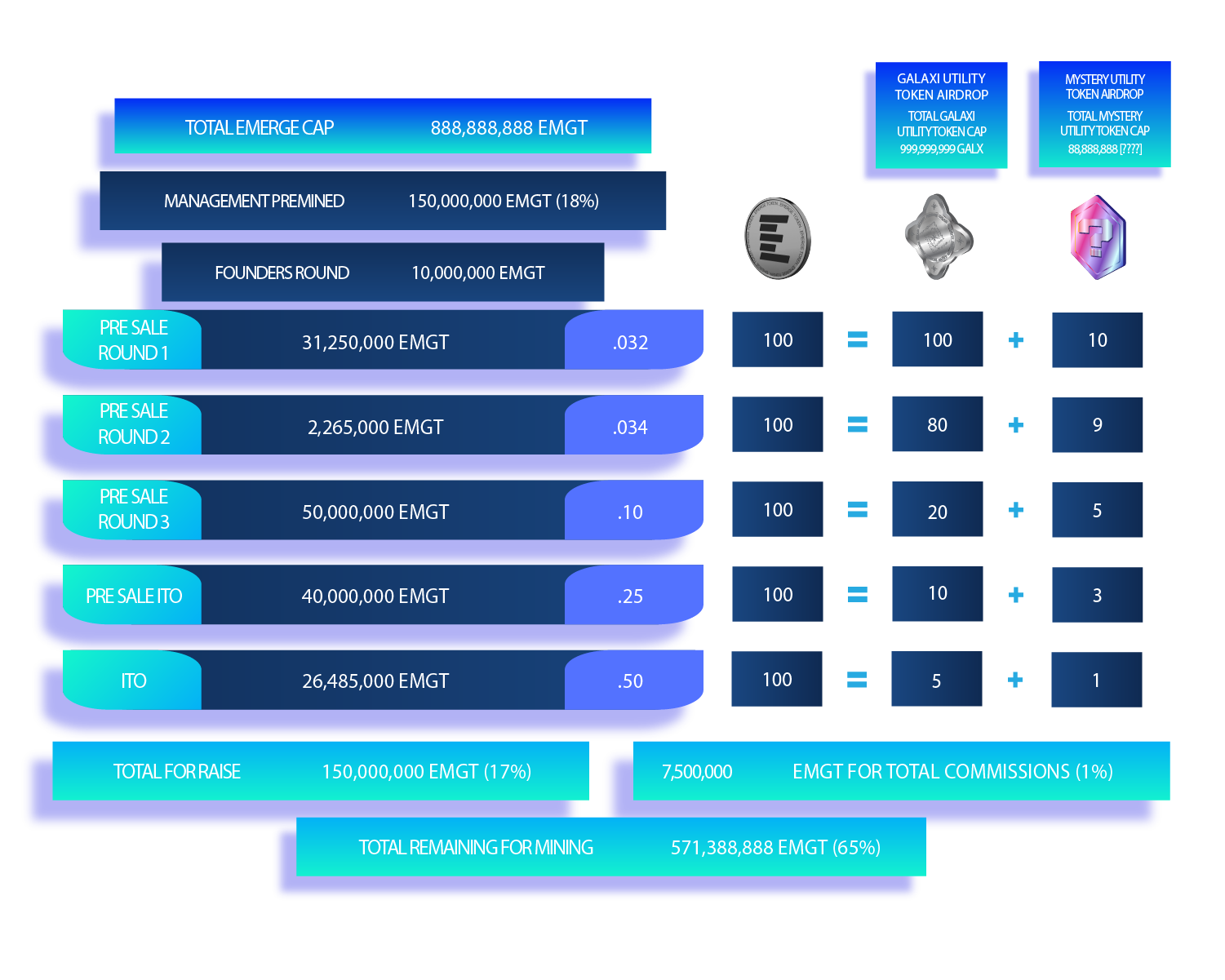
- TOKEN PRE-SALE ROUND 1-2
- FORM LLC & COMPLETE COMPLIANCE DOCS WITH THE STATE OF WYOMING
- COMPLETE ALL MARKETING MATERIALS FOR WEBSITE, WHITEPAPER, ETC
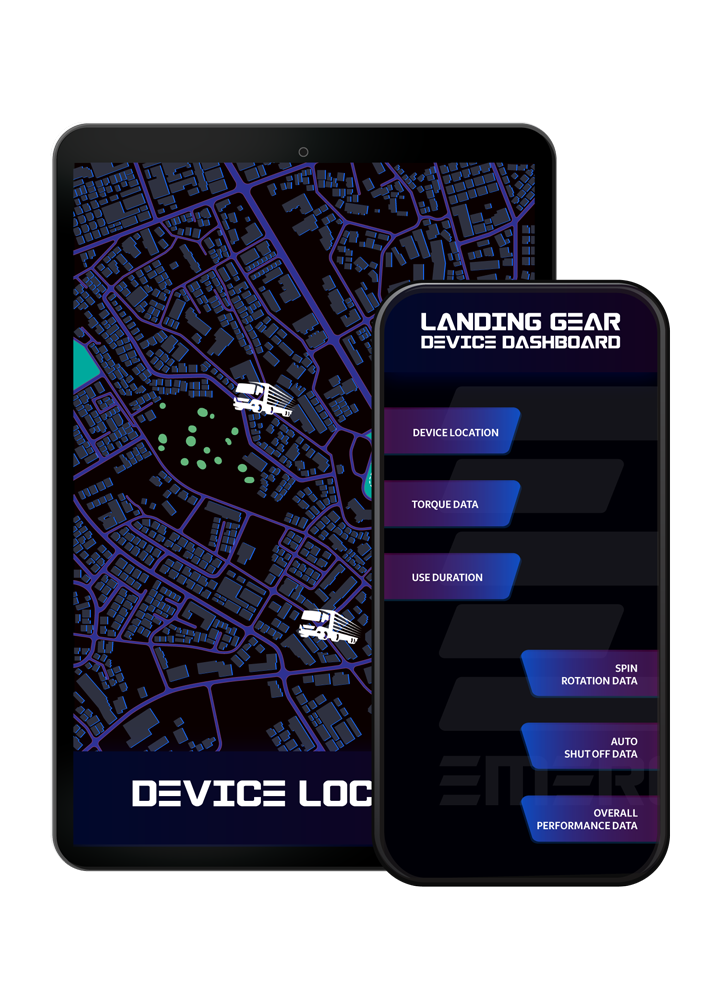
- PROGRAMMING FOR DATA SETS: DEVICE LOCATION, TORQUE DATA, USE DURATION
- SPIN ROTATIONS, AUTO SHUTOFF, OVERALL PERFORMANCE
- INITIATE GALAXI WALLET DEVELOPMENT & REVEAL PARTIAL DETAILS.
- MARKETING VIDEOS AND SOCIAL MEDIA DEVELOPMENT
- MARKETING TEAM
- CONTINUE PHASE 1 SOFTWARE DEVELOPMENT
- CONTINUE MARKETING VIDEOS AND SOCIAL MEDIA DEVELOPMENT
- INITIATE GAME APP CONCEPT VOTING AND DEVELOPMENT
- SOLONA NETWORK PHASE
- LAUNCH OF PRE SALE ROUND 3
- COMPLETE PHASE 1 SOFTWARE DEVELOPMENT
- REVEAL “MYSTERY TOKEN” AIRDROP DETAILS
- REVEAL FULL UTILITY DETAILS OF GALAXI WALLET
- INITIATE AND FINALIZE CHARITY PARTNERSHIP
- REMOTE AND CLOUD API
- INITIATE AND COMPLETE PHASE 1 SOFTWARE TESTING ULTRALIFT’S
- HARDWARE TO VALIDATE AND FINALIZE DEVELOPMENT
- INTEGRATION WITH BLOCKCHAIN
- ALGORITHM FOR MINING
- INITIATE DISCUSSIONS WITH MAJOR CAPITAL GROUPS
- COMPLETE AND TEST GALAXI WALLET
- TESTING FOR SOFTWARE DEVELOPMENT WITH ULTRALIFT’S HARDWARE
- TOKEN MINING TEST
- DATA RECORDING AND TRANSFER TEST
- USER PLATFORM TEST & ERRORS/FIX TEST
- CONTINUE GALAXI WALLET CODING
- FINALIZE PARTNERSHIPS WITH MAJOR CAPITAL GROUPS
- MARKETING CAMPAIGN INTRODUCING WORLD’S FIRST DATA-DRIVEN SMART POWERTOOL
- REVEAL “MYSTERY TOKEN” AIRDROP DETAILS
- ITO ROUND
- BETA RELEASE WITH ULTRALIFT FOR EXISTING ULTRALIFT’S CLIENTS
- INITIATE FIELD DEMO TRIAL WITH INTERESTED INSURANCE COMPANIES
- INITIATE MAJOR EXCHANGE LISTINGS
- AIRDROP “MYSTERY TOKEN”
- REVEAL FUTURE ROADMAP
- ESTABLISH DEVELOPMENT GOALS WITH EMERGE LABS
- ULTRALIFT AND EMERGE
- INITIATE DESIGN CONCEPTS FOR SMART POWER TOOL
- INITIATE SMART POWERTOOL DEVELOPMENT
- HARDWARE & SOFTWARE
- CONTINUE SMART POWERTOOL DEVELOPMENT
- INITIATE CIRCUITRY DESIGN
- BOM (BILL OF MATERIALS)
- CONTINUE SMART POWERTOOL DEVELOPMENT
- COMPLETE CIRCUITY DESIGN
- FEEDBACK FROM EXISTING CLIENTS REGARDING DESIGN
- BOM ( BILL OF MATERIALS )
- CONTINUE SMART POWER TOOL DEVELOPMENT
- FINALIZE DESIGN BASED ON EXISTING CLIENT’S FEEDBACK
- FINALIZE BOM (BILL OF MATERIALS)
- COMPLETE SMART POWERTOOL DEVELOPMENT
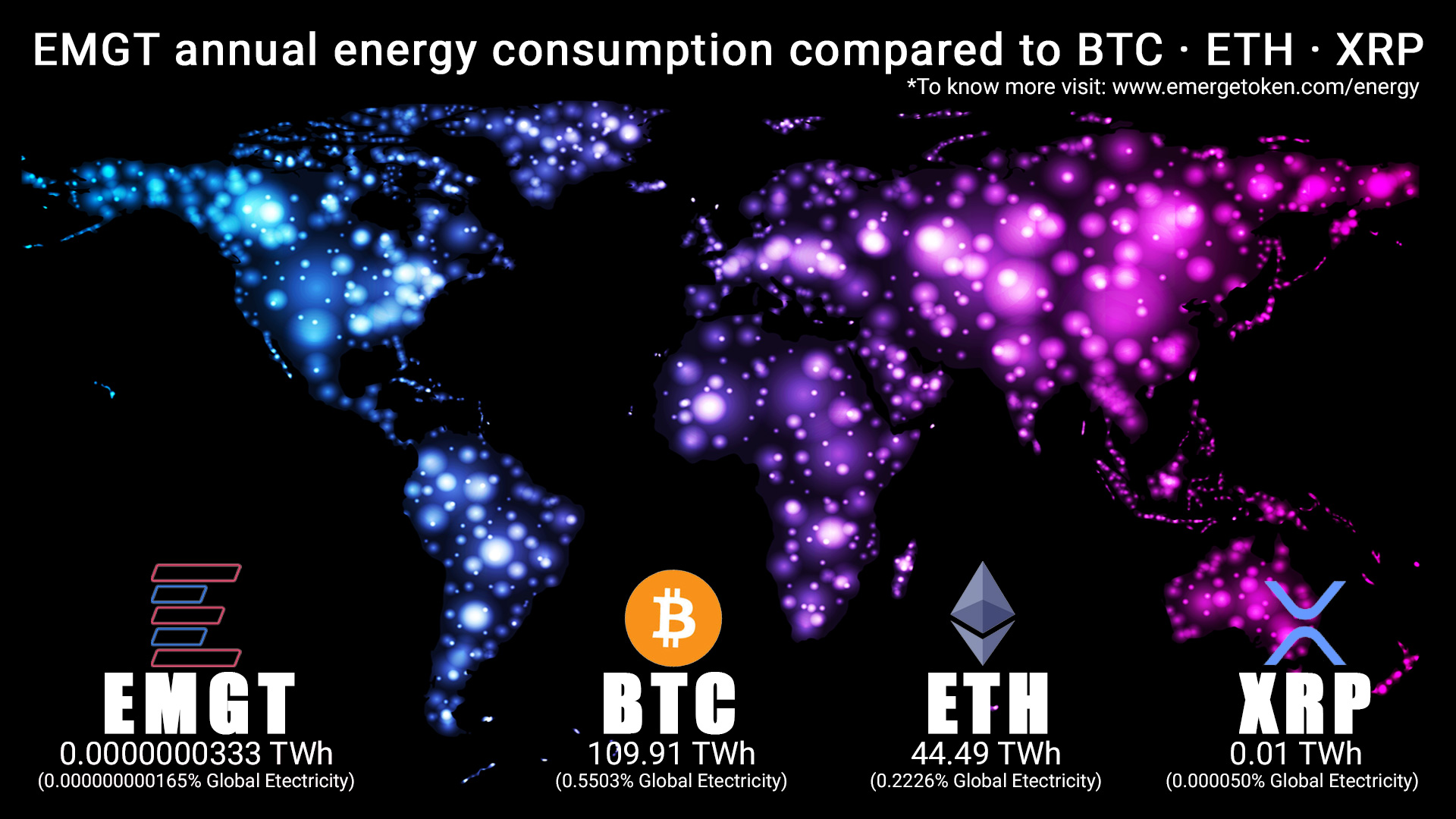
- CONVERT NETWORK TO SOLANA PLATFORM FROM ETHEREUM
- INITIATE SMART POWERTOOL PROTOTYPE PROCESS
- BEGIN CODING FOR BROWSER EXTENSION FOR GALAXI WALLET
- INITIATE MECHANICAL, ELECTRICAL & ENVIRONMENTAL TESTING OF SMART POWERTOOL PROTOTYPE
- INITIATE AND COMPLETE PHASE 1 FOR SOFTWARE TESTING
- ULTRALIFT’S HARDWARE TO VALIDATE AND FINALIZE DEVELOPMENT
- INITIATE & COMPLETE PHASE 1 SOFTWARE TESTING WITH ULTRALIFT’S HARDWARE
- ASSIST EMERGE TEAM ON PHASE 2 OF ULTRALIFT’S HARDWARE
- INITIATE DISCUSSIONS WITH MAJOR CAPITAL GROUPS
- ASSIST AND COMPLETE TESTING FOR EMERGE’S PHASE 2 HARDWARE SOFTWARE DEVELOPMENT
- FINALIZE PARTNERSHIPS WITH MAJOR CAPITAL GROUPS
- INITIATE MARKETING CAMPAIGN INTRODUCING WORLD’S FIRST DATA-DRIVEN SMART POWERTOOL
- BETA RELEASE WITH EMERGE FOR EXISTING ULTRALIFT’S CLIENTS
- INITIATE FIELD DEMO TRIAL WITH INTERESTED INSURANCE COMPANIES AND FLEETS
- REVEAL FUTURE ROADMAP